example 4 honeypot
Example of a sustainability analysis - Analyzing time-to-exploit of exposed credentials in public code repositories: a controlled study using honeypot infrastructure
Analyzing time-to-exploit of exposed credentials in public code repositories: a controlled study using honeypot infrastructure
Authors: Christina Alexandra Giltvedt-Winness, Lida Victoria Johnsen, Miriam Harestad Linna, Vetle Pettersen
Short description
Topic: Honeypot solution for collecting and analyzing data on how leaked login credentials are discovered and exploited
Type of assignment: Cybersecurity, analysis of attack patterns
Summary
Millions of credentials are leaked through public code repositories each year. Exploitation of these exposed secrets can cause devastating consequences for both large and well-established actors, as well as smaller startups. Open-source developer platforms such as GitHub provide proprietary secret detection frameworks intended to protect against these exposures. Despite this, the platform experienced 39 million accidental credential leaks in 2024.
This thesis explores differences in attacker preferences for various types of credentials, measured by their Time-to-Exploit (TTE). In addition, the study identifies attack profiles based on observable characteristics of malicious actors searching for exposed secrets. A series of tests were conducted to identify gaps in GitHub’s secret detection framework.
The results show that attackers strongly favor ease of access. Brute force attack methods were prioritized over searching for leaked secrets when attempting to breach SSH and RDP-enabled virtual machines. For credential types more resistant to brute force attacks, attackers instead relied on credential scanning methods to detect connection strings with clear and uniform structures. Credentials discovered in this way had an average Time-to-Exploit of six to seven minutes, indicating the use of web crawling and scraping techniques to efficiently process newly uploaded data.
Sustainability analysis
At first glance, this assignment may appear unrelated to sustainability, as it focuses on how leaked login credentials are discovered and exploited. However, improved digital security contributes to a safer and more stable society by reducing the risk of data breaches, financial losses, and misuse of sensitive information.
The analysis is based on a honeypot system designed to collect and study data on how attackers discover and exploit exposed credentials. This system enables insight into how quickly attackers react to leaked keys and how effective current security mechanisms are.
Assumptions in the analysis:
- The honeypot works as intended and collects reliable data.
- Developers and security researchers will use the results to improve security.
The following sections present a SusAF analysis, showing positive and negative
sustainability impacts in five areas: technical, social, individual, environmental and economic.
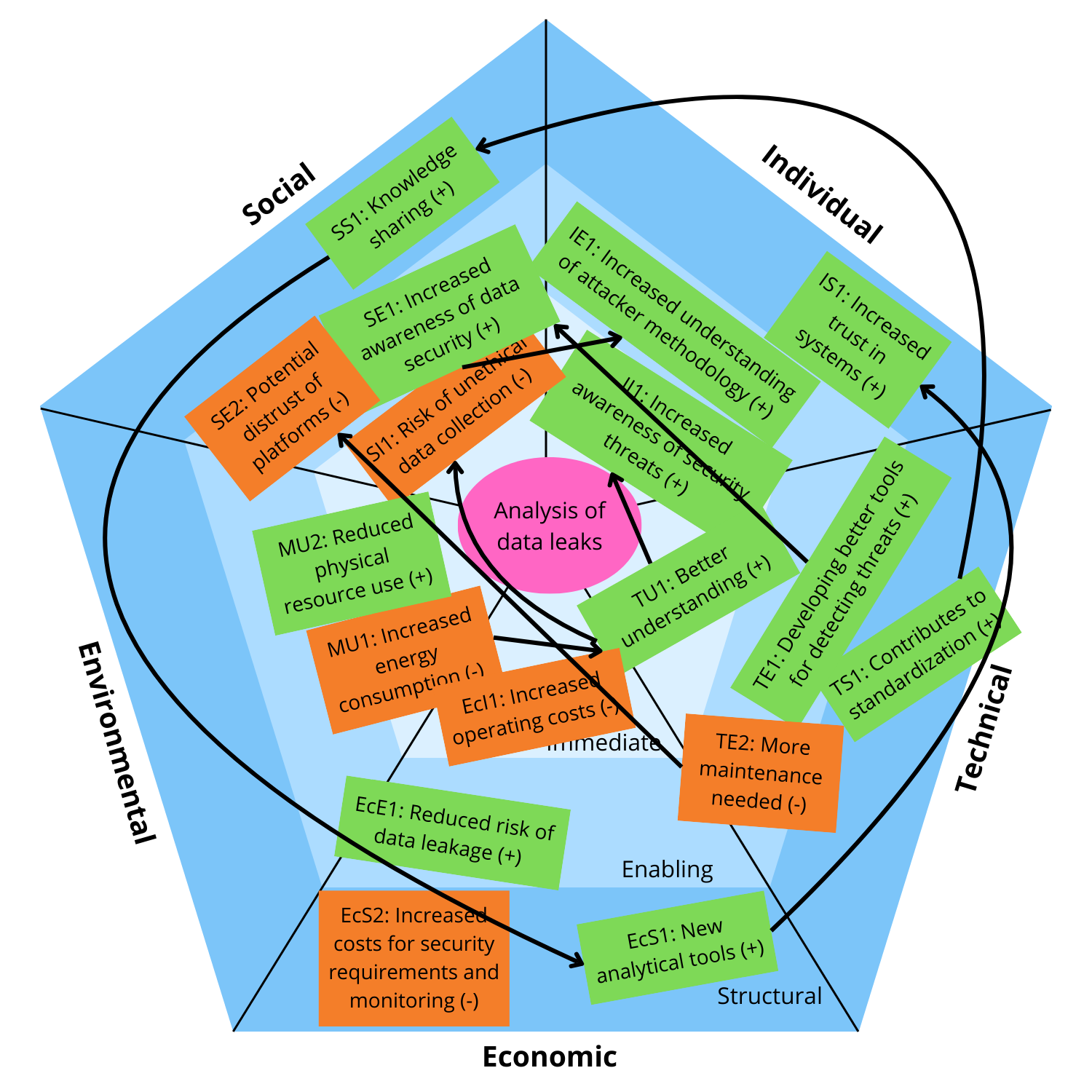
In the middle of the SusAF analysis
At the center of the model is the honeypot technology and how it is introduced. The analysis
looks both at the technology itself and how people use it.
Technical Dimension
This dimension describes how the honeypot affects digital systems and their development
Technical Dimension
This dimension describes how the honeypot affects digital systems and technological development.
|
Technical impacts, immediate; positive
|
|
Technical impacts, enabling; positive
|
|
Technical impacts, enabling; negative
|
|
Technical impacts, systematic; positive
|
Social Dimension
This dimension examines how the project affects trust, collaboration, and ethics within society and the IT sector.
|
Social impacts, immediate
|
|
Social impacts, enabling; positive
|
|
Social impacts, enabling; negative
|
|
Social impacts, systematic
|
Individual Dimension
This dimension focuses on how the project affects individuals’ safety and understanding of digital security.
|
Individual impacts, immediate; positive
|
|
Individual impacts, enabling; positive
|
|
Individual impacts, systematic; positive
|
Environmental Dimension
|
Environmental impacts, immediate; negative
|
|
Environmental impacts, immediate; positive
|
Economic Dimension
|
Economic impacts, immediate; negative
|
|
Economic impacts, enabling; positive
|
|
Economic impacts, systematic
|
Relationships Between Impacts
Some impacts lead to others:
Immediate relationships
TI1 → II1: More developer knowledge also increases individual awareness.
TI1 →SI1: Knowing more about GitHub’s security also highlights risks of misuse.
MI1 → ØI1: Higher energy use directly increases costs.
Enabling relationships
TM1 → SM1: Better tools make it easier to communicate risks and raise awareness.
SM1 → IM1: Increased public focus helps individuals learn more about threats.
TM2 → SM2: Poor maintenance may lead to distrust in platforms like GitHub.Systematic relationships
SS1 → ES1: More shared knowledge leads to greater industry investment in security.
TS1 → SS1: Standardized methods make it easier to share data and collaborate.
ES1 → IS1: Stronger long-term security increases user trust.
This is how the table can be presented:
| ID | Impact | Level | Affects | + / - |
|---|---|---|---|---|
| TI1 | Improved understanding of GitHub’s security features | Immediate | SI1, II1 | + |
| TE1 | Enables development of improved threat detection tools, such as enhanced AI-based systems | Enabling | SE1 | + |
| TE2 | Increased need for maintenance and monitoring | Enabling | SE2 | - |
| TS1 | Strengthens standardization of honeypot methodologies and may form the basis for new guidelines and research tools | Structural | SS1 | + |
| II1 | Increased awareness of security threats | Immediate | + | |
| IE1 | Improved understanding of attacker methodologies | Enabling | + | |
| IS1 | Increased trust and confidence in continuously improving systems | Structural | + | |
| SI1 | Risk of unethical data collection that could be misused by attackers | Immediate | - | |
| SE1 | Increased societal awareness of data security, such as how quickly leaked credentials are exploited | Enabling | IE1 | + |
| SE2 | Potential distrust in open development platforms such as GitHub | Enabling | - | |
| SS1 | Facilitates knowledge sharing between research communities and the IT industry | Structural | ES1 | + |
| EnI1 | Increased energy consumption due to continuous operation and logging | Immediate | EI1 | - |
| EnI2 | Reduced physical resource usage due to cloud-based honeypot infrastructure | Immediate | + | |
| EI1 | Costs related to cloud operation and data storage | Immediate | - | |
| EcE1 | Reduced risk of financial loss from data breaches due to earlier detection | Enabling | + | |
| ES1 | Increased focus on security breaches, potentially leading to development of new analysis tools | Structural | IS1 | + |
| ES2 | Increased costs related to security requirements and monitoring | Structural | - |






