Cyber-physical systems security Lab
Cyber-Physical Systems Security Lab
Cyber-physical systems security is crucial for ensuring the safety, reliability, and resilience of critical infrastructures. The Cyber-physical Systems Security Lab at NTNU conducts advanced research on developing secure and reliable CPS, focusing on design, analysis, and implementation. The lab’s research topics include, but are not limited to, security by design, anomaly detection, intrusion prevention, attack mitigation, risk assessment, and privacy preservation for CPS. The lab also develops novel tools and techniques for modeling, simulation, verification, and testing of CPS security. The lab collaborates with industrial and academic partners as well as government agencies to address the real-world challenges and needs of CPS security in several sectors, including but not limited to manufacturing, power, maritime, and healthcare.
Research Directions
The lab can be utilized to validate assumptions regarding the security postures of cyber physical systems. This facilitates the conducting of informed cyber risk assessment. The lab facilitates the investigation of adversarial capacity to establish Command and Control (C2C) channels in maritime systems"
Related Publications:
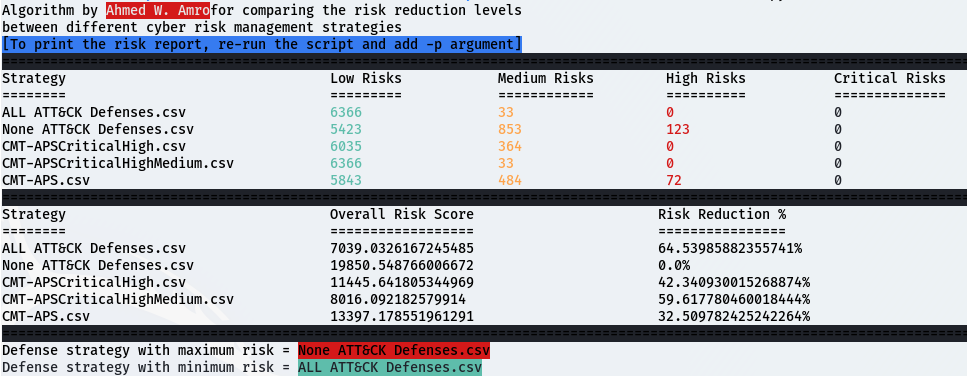
- Amro, A., Gkioulos, V., & Katsikas, S. (2023). Assessing cyber risk in cyber-physical systems using the ATT&CK framework. ACM Transactions on Privacy and Security, 26(2), 1-33.
- Oruc, A., Amro, A., & Gkioulos, V. (2022). Assessing cyber risks of an INS using the MITRE ATT&CK framework. Sensors, 22(22), 8745.
- Amro, A., & Gkioulos, V. (2023). Evaluation of a Cyber Risk Assessment Approach for Cyber–Physical Systems: Maritime-and Energy-Use Cases. Journal of Marine Science and Engineering, 11(4), 744.
- Oruc, A., Kavallieratos, G., Gkioulos, V., & Katsikas, S. (2024). Cyber Risk Assessment for SHips (CRASH).
- Spathoulas, Georgios, et al. "Attack path analysis and cost-efficient selection of cybersecurity controls for complex cyberphysical systems." European Symposium on Research in Computer Security. Cham: Springer International Publishing, 2021
- Kavallieratos, Georgios, Vasiliki Diamantopoulou, and Sokratis K. Katsikas. "Shipping 4.0: Security requirements for the cyber-enabled ship." IEEE Transactions on Industrial Informatics 16.10 (2020): 6617-6625
- Kavallieratos, Georgios, et al. "Risk assessment and control selection for cyber-physical systems: A case study on supply chain tracking systems." (2022).
- Akbarzadeh, A., & Katsikas, S. K. (2023). Dependency-based security risk assessment for cyber-physical systems. International Journal of Information Security, 22(3), 563-578
The lab facilitates the investigation of adversarial capacity to establish Command and Control (C2C) channels in maritime systems over VHF communication, particularly, the Automatic Identification System. Attackers can utilize this channel to send commands and files to air-gapped systems within maritime systems (e.g. vessels, VTS).
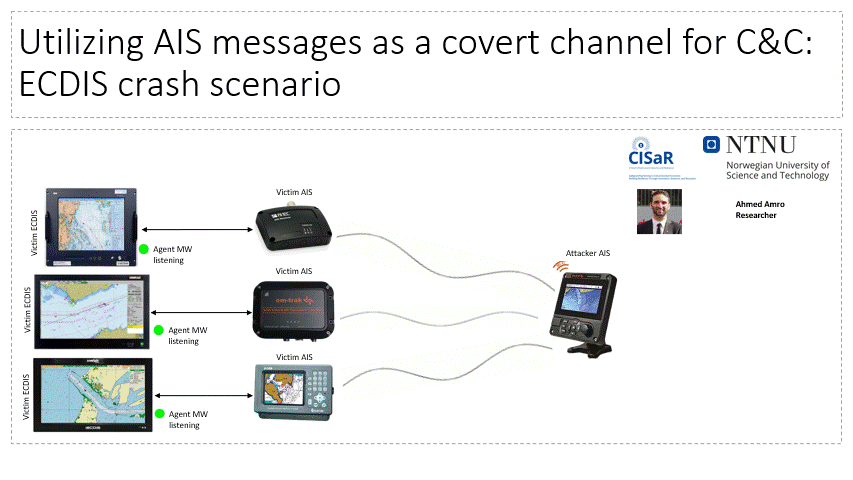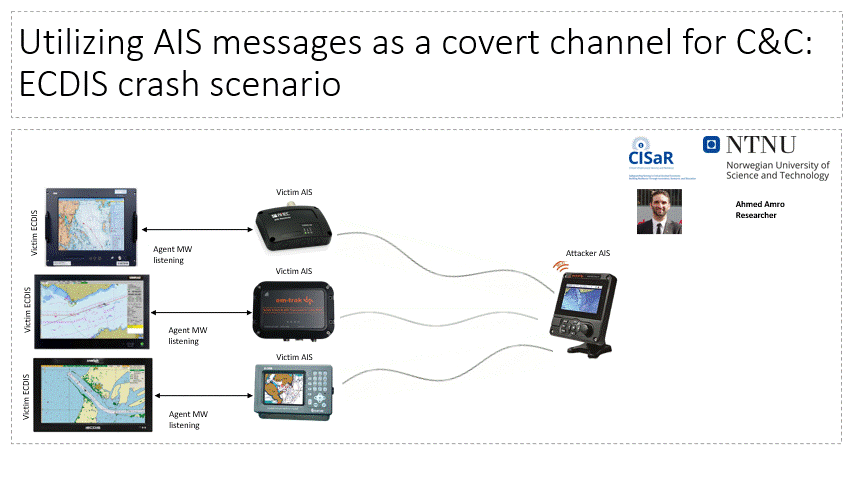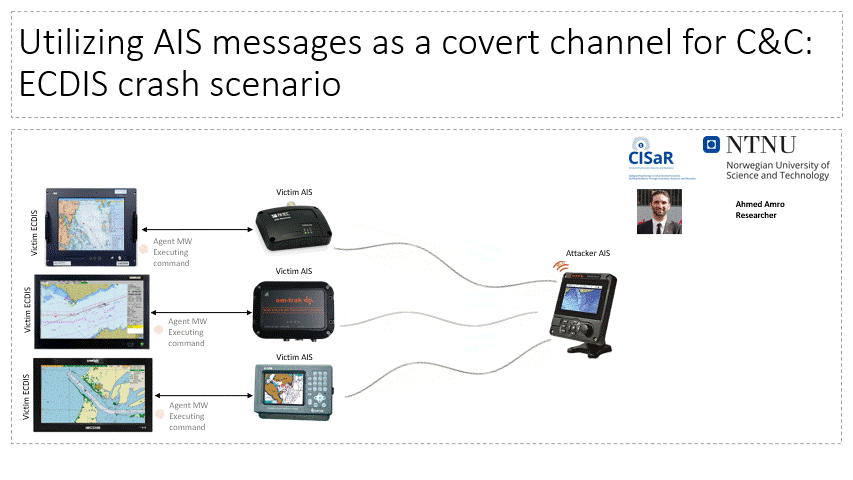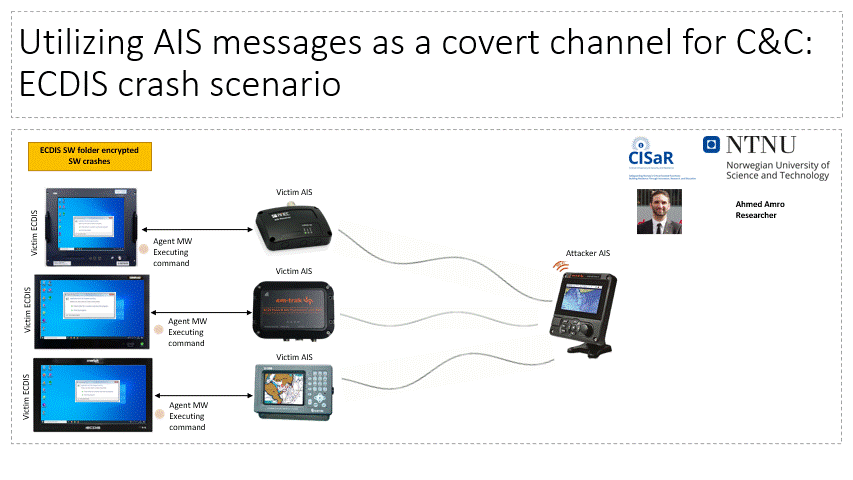
Related Publications:
- Amro, A., & Gkioulos, V. (2022, September). From click to sink: Utilizing ais for command and control in maritime cyber attacks. In European Symposium on Research in Computer Security (pp. 535-553). Cham: Springer Nature Switzerland.
The testing environment can be used to realize different attacks. The ship view is produced using the bridge command simulator, which is utilized as the NMEA sender. The simulator includes a simulated GPS device sending NMEA messages over UDP to the listener. On the other hand, the chart plotter view is produced by the OpenCPN chart plotter software, which is utilized as the NMEA listener. Moreover, 𝑊𝑖𝑟𝑒𝑠ℎ𝑎𝑟𝑘 is utilized for capturing the network traffic at the receiving node. The attacker node operates the Kali Linux operating system with the NMEA-Manipulator system.
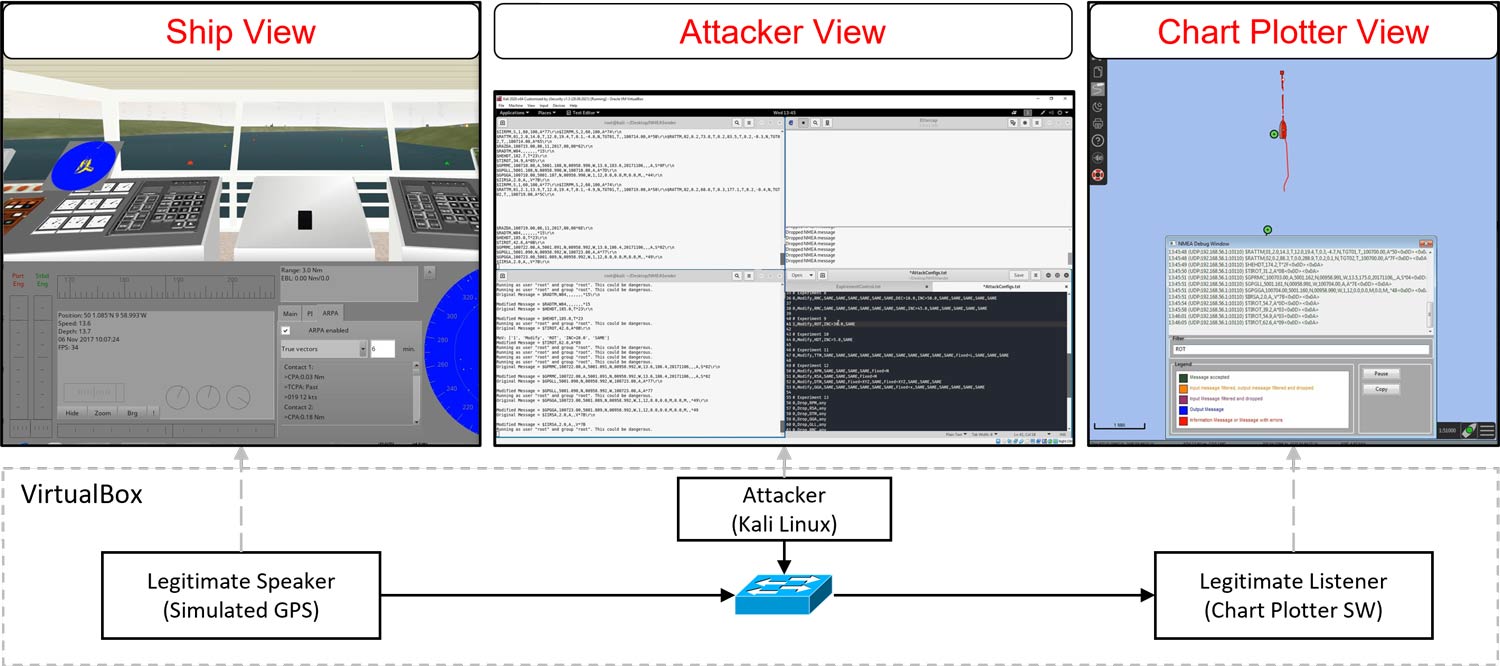
Related Publications:
- Amro, A., Oruc, A., Gkioulos, V., & Katsikas, S. (2022). Navigation data anomaly analysis and detection. Information, 13(3), 104.
The lab incorporates a group of tools for replicating several system elements such as hardware or data streams. This includes tools for simulating entire infrastructure such as GNS3, and tools for simulating navigation functions and data such as bridge command. Also, the lab incorporates tools and scripts for simulating cyber attacks using customized or open-source tools such as Caldera.
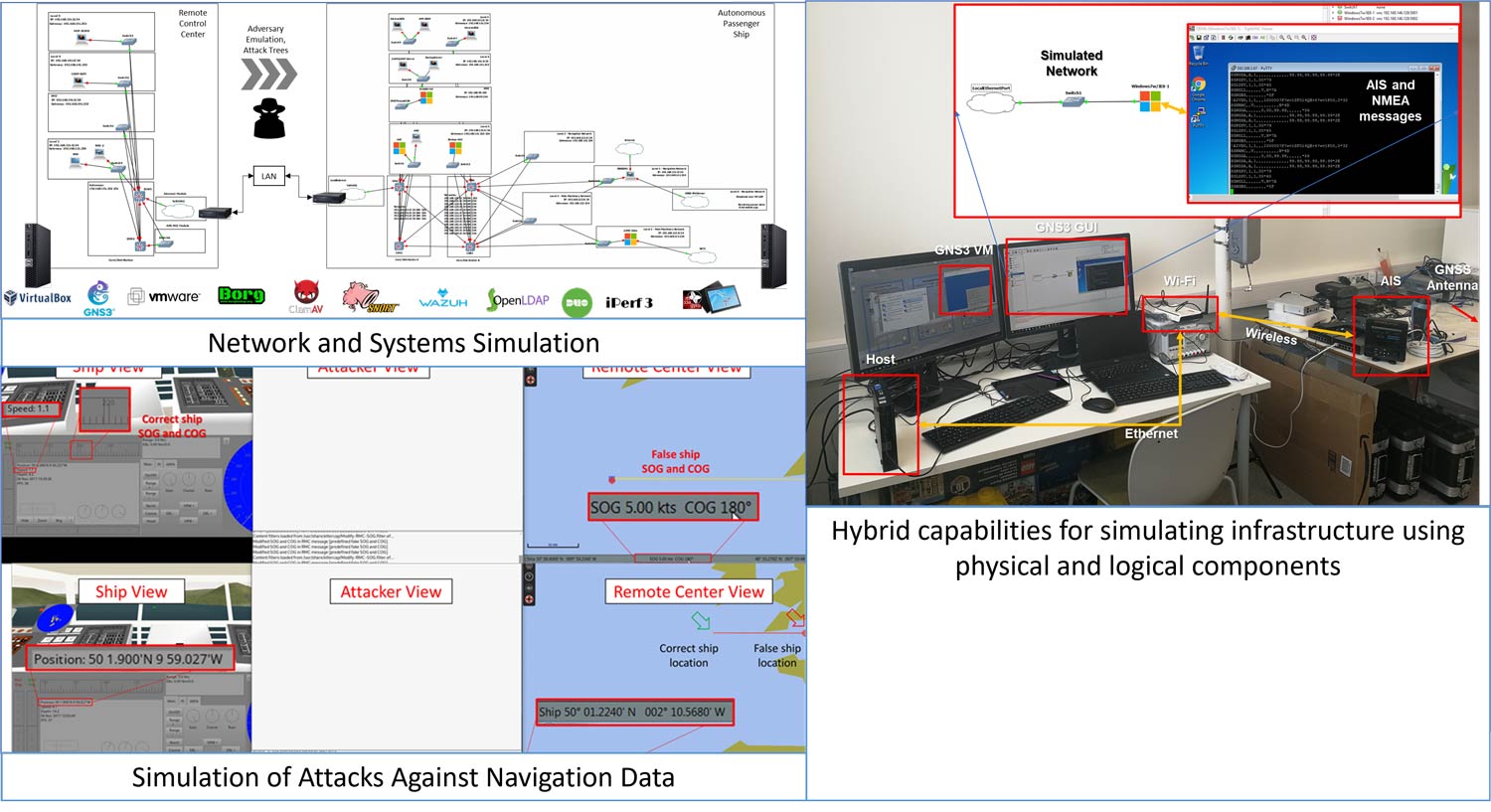
Related Publications:
- Amro, A., & Gkioulos, V. (2021, October). Communication and cybersecurity testbed for autonomous passenger ship. In European Symposium on Research in Computer Security (pp. 5-22). Cham: Springer International Publishing.
- Amro, A., Gkioulos, V., & Katsikas, S. (2023). Communication architecture for autonomous passenger ship. Proceedings of the Institution of Mechanical Engineers, Part O: Journal of Risk and Reliability, 237(2), 459-484.
- Amro, A., & Gkioulos, V. (2023). Cyber risk management for autonomous passenger ships using threat-informed defense-in-depth. International Journal of Information Security, 22(1), 249-288.
The lab facilitates several reconnaissance methods against cyber-physical systems. This includes a variety of open-source tools as well as customized tools that have been developed specifically for maritime systems. An example of such is the utilization of Shodan for detecting maritime devices broadcasting NMEA or AIS devices
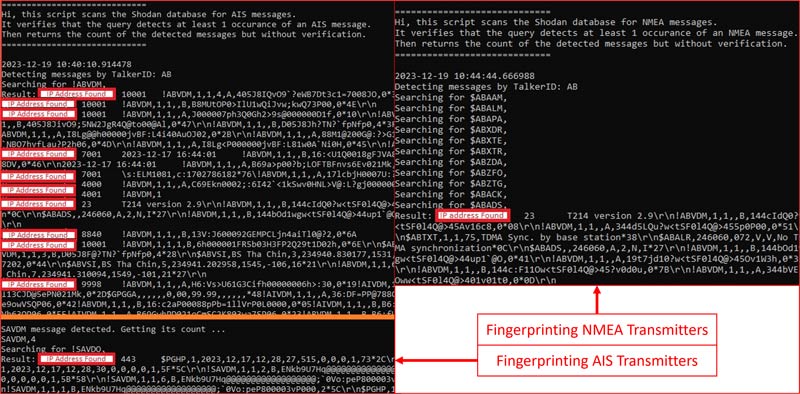
Related Publications:
- Amro, A. (2021). Cyber-Physical Tracking of IoT devices: A maritime use case. In Norsk IKT-konferanse for forskning og utdanning (No. 3).
The lab can be utilized for a variety of security evaluation processes including penetration testing for systems within the lab as well as remote systems interfaced with the lab network using virtual networking. An example of such projects included the penetration testing of an autonomous passenger ferry physically (using tools developed within the lab) and remotely from the lab facilities in Gjøvik evaluating the ferry in Trondheim.
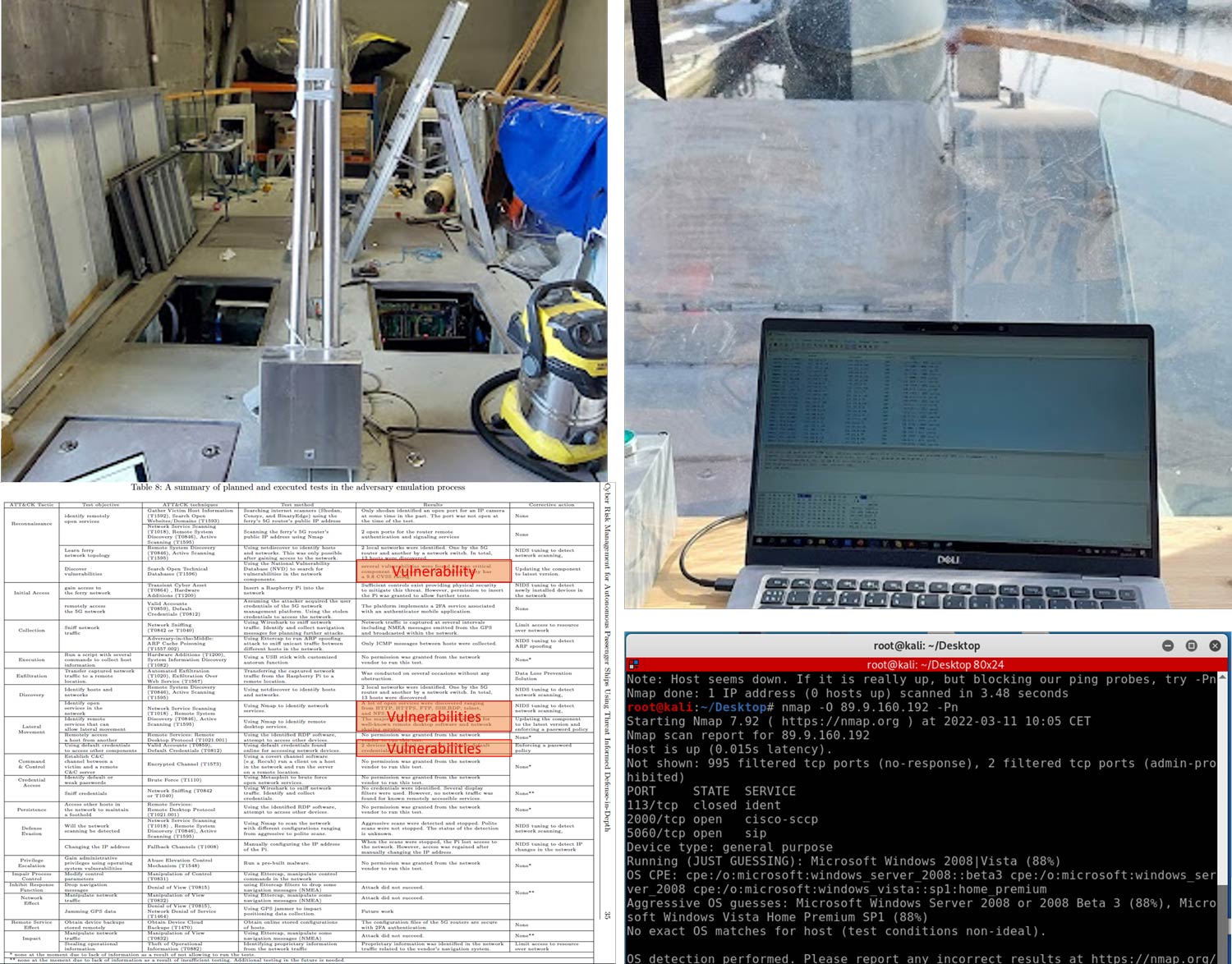
Related Publications:
- Amro, A., & Gkioulos, V. (2023). Cyber risk management for autonomous passenger ships using threat-informed defense-in-depth. International Journal of Information Security, 22(1), 249-288.
- Grammatikis, P. R., Sarigiannidis, P., Dalamagkas, C., Spyridis, Y., Lagkas, T., Efstathopoulos, G., ... & Arce, A. (2021). Sdn-based resilient smart grid: The sdn-microsense architecture. Digital, 1(4), 173-187.
Related Publications:
- B. Heluany, J., & Gkioulos, V. (2023, August). Survey on Digital Twins: from concepts to applications. In Proceedings of the 18th International Conference on Availability, Reliability and Security (pp. 1-8).
Lab's equipment
- AIS A200
- AIS B921
- Furunu GP 170
- Garmin NMEA 2000 network starter kit
- Garmin NMEA 2000 Network Updater
- Maretron IPG100
- Cisco Aironet 1532E
- Cisco Wireless Controller 3504
- Netgear Nighthawk Mobile Hotspot Router
- Cisco RV042G
- Omnicharge Ultimate
- 9V power bank
- SDRplay RSPdx
- ADALM-PLUTO
CPS lab has a wide variety of equipment, that can be used for variuos projects, in different areas, like Manufacturing, IoT, Healthcare and Smart soceity.
The following is a brief list of the equipments the lab contains:
- Demonstrators
- Communication boards
- Interfacing equipment
- Audio and Voice equipment
- Health care sensors
- Antennas
- Microcontrollers
- 3D printer
- Human Machine Interface (HMI)
Projects
-
CYBERUNITY
-
FACT
-
NEWSROOM
Contact person
Lab's partners and funding resources